

Modernizacja systemów nie jest projektem technologicznym. To inicjatywa mająca na celu przetrwanie firmy, przebrana za prace inżynieryjne. W Grupie SKM postrzegamy transformację systemów jako kontrolowaną eliminację ryzyka – przeprowadzaną z precyzją, powściągliwością i głębokim szacunkiem dla tego, co już działa. Nie próbujesz „przepisać przeszłości”.Starasz się chronić przyszły wzrost, jednocześnie utrzymując przy życiu obecne operacje.
Modernizacja oprogramowania legacy to ustrukturyzowana ewolucja istniejących systemów, które nadal obsługują podstawowe procesy biznesowe, ale nie spełniają już dzisiejszych wymagań dotyczących skalowalności, bezpieczeństwa, integracji ani szybkości. W środowiskach korporacyjnych „tradycyjne” nie oznacza starego – oznacza krytyczne. Systemy te często przetwarzają przychody, dane klientów, przepływy pracy związane z zapewnieniem zgodności oraz logikę operacyjną budowaną przez dekady.
Z naszej perspektywy w Grupie SKM, modernizacja nie jest przełącznikiem binarnym. To ciągła, zarządzana ryzykiem podróż, w której architektura, dane, infrastruktura i ludzie wspólnie się rozwijają. Zarządzanie ryzykiem modernizacji starszego oprogramowania to dyscyplina, która gwarantuje, że ta podróż nie zakłóci działalności Twojej firmy, nie nadszarpnie zaufania ani nie stworzy nowych problemów technicznych, jednocześnie rozwiązując stare.
Modernizujemy się nie dlatego, że technologia jest przestarzała, ale dlatego, że koszt braku modernizacji jest wyższy niż ryzyko zmiany.
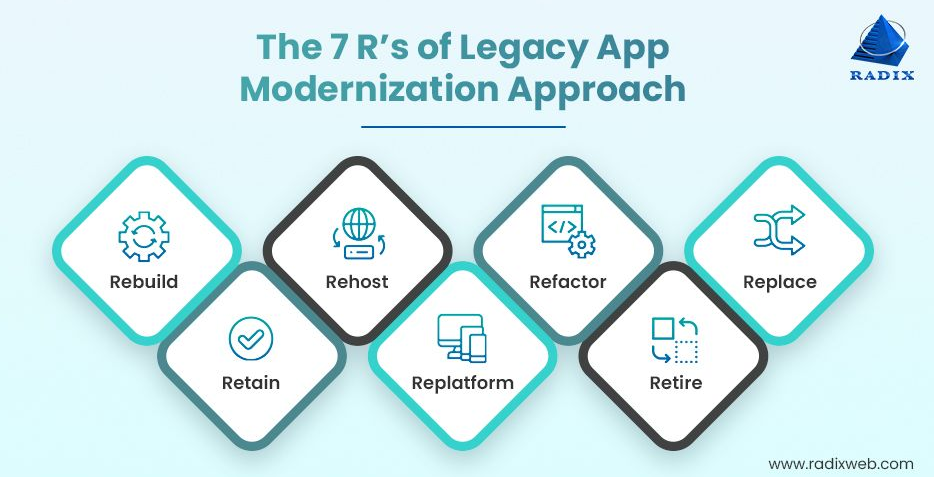
Większość błędów w modernizacji starszych modeli przebiega według tych samych, przewidywalnych schematów. Rzadko są one spowodowane pojedynczą złą decyzją. Wynikają z nagromadzonych ślepych punktów, które z czasem się pogłębiają.
Do najczęstszych obserwowanych przez nas błędów należą: niedoszacowanie złożoności systemu, brakujące zależności ukryte w monolitycznych bazach kodu, pospieszna migracja danych oraz zbyt późne włączanie interesariuszy biznesowych. Organizacje często traktują modernizację jako problem IT, ignorując, jak głęboko starsze systemy są powiązane z operacjami, finansami i zgodnością z przepisami.
Kiedy pojawiają się te wzorce, zespoły reagują zamiast kontrolować. Terminy się przesuwają, budżety rosną, a plany wycofania przekształcają się w permanentne tryby awaryjne. Aby uniknąć niepowodzeń w modernizacji starszych systemów, należy wcześnie rozpoznać te wzorce i opracować strategię opartą na nich, nie licząc na to, że nie będą miały zastosowania w Twoim przypadku.
Uwolnij swoje wewnętrzne zespoły, aby mogły skupić się na strategii dzięki niezawodnym rozwiązaniom outsourcing IT.
Dług techniczny nie jest abstrakcyjny. Jest przechowywany w nieudokumentowanej logice, przestarzałych frameworkach, niestabilnych integracjach i modelach danych, którym nikt w pełni nie ufa. Każdy starszy system go nosi, a modernizacja go ujawnia.
Ryzyko pojawia się, gdy dług jest ignorowany zamiast nim zarządzać. Działania modernizacyjne, które polegają na prostym „przeniesieniu” starszych systemów na nowe platformy bez zajmowania się długiem strukturalnym, prowadzą do szybszych i bardziej kosztownych awarii. Infrastruktura chmurowa nie naprawia złej architektury, lecz ją wzmacnia.
W Grupie SKM traktujemy dług techniczny jako mierzalny czynnik ryzyka. Zarządzanie nim jest kluczowe dla minimalizacji ryzyka związanego z modernizacją istniejących systemów , ponieważ dług bezpośrednio wpływa na stabilność, przewidywalność i długoterminową kontrolę kosztów.
Modernizacja systemów tradycyjnych wprowadza zmiany do systemów zaprojektowanych tak, aby się im opierać. Zarządzanie ryzykiem to klucz do kontroli nad tymi zmianami. Bez niego modernizacja staje się serią niepowiązanych ze sobą eksperymentów technicznych, które Twoja firma traktuje jako obciążenie operacyjne.
Skuteczne zarządzanie ryzykiem pozwala na:
Dlatego redukcja ryzyka związanego z modernizacją nie jest sloganem, lecz nakazem operacyjnym. Ryzyko nie znika. Ono się przemieszcza. Twoim zadaniem jest zdecydować, gdzie ono jest i jak bardzo jest widoczne.
Starsze systemy rzadko funkcjonują w izolacji. Są one powiązane z procesami biznesowymi, partnerami zewnętrznymi, procesami raportowania i ograniczeniami infrastrukturalnymi. Te zależności zwielokrotniają ryzyko modernizacji, ponieważ zmiany w jednym obszarze mogą rozprzestrzenić się na całą organizację.
Najbardziej niebezpieczne zależności są często niewidoczne:
Jeśli te zależności nie zostaną odpowiednio wcześnie zmapowane, modernizacja staje się reaktywna. W Grupie SKM kładziemy nacisk na ich ujawnianie przed podjęciem decyzji dotyczących architektury, a nie po wystąpieniu incydentów.
Identyfikacja komponentów wysokiego ryzyka w architekturach monolitycznych
Systemy monolityczne koncentrują ryzyko. Niewielka zmiana może mieć duży wpływ, ponieważ komponenty są ściśle ze sobą powiązane. Identyfikacja obszarów wysokiego ryzyka oznacza zrozumienie, które moduły obsługują krytyczne dane, które ulegają najczęstszym zmianom, a które ulegają cichym awariom.
Nie należy modernizować wszystkiego naraz. W pierwszej kolejności należy modernizować to, co zagraża stabilności. Prawidłowa ocena ryzyka modernizacji starszych systemów klasyfikuje komponenty według wpływu na działalność, częstotliwości zmian i promienia rażenia awarii, umożliwiając bezpieczną sekwencję transformacji.
Analiza portfolio aplikacji dla starszych systemów
Decyzji dotyczących modernizacji nigdy nie należy podejmować oddzielnie dla każdego systemu. Analiza portfela aplikacji zapewnia makroskopowy obraz ekosystemu – co zmodernizować, wycofać, wymienić, a co zachować.
Ta analiza pomaga zrozumieć redundancję, dublowanie i ukryte koszty. Ujawnia również, gdzie modernizacja przynosi realną wartość biznesową, a gdzie jedynie kosmetyczne usprawnienia techniczne. W Grupie SKM analiza portfela to miejsce, w którym strategia opiera się na rzeczywistości operacyjnej.
Ocena integralności danych i ryzyka migracji
Dane to najdelikatniejszy zasób w modernizacji. Kod można przepisać. Infrastrukturę można wymienić. Raz uszkodzone dane często są nie do odzyskania.
Ocena ryzyka migracji koncentruje się na własności danych, ich jakości, pochodzeniu i wymaganiach dotyczących synchronizacji. Musisz wiedzieć, które systemy są źródłem prawdy, jak weryfikowane są dane i jak rozwiązywane są niespójności. Modernizacja bez zdyscyplinowanego planowania danych to najszybsza droga do zakłóceń w działalności.
Ocena ryzyka bezpieczeństwa i zgodności podczas modernizacji
Starsze systemy często opierają się na przestarzałych modelach bezpieczeństwa, ale mogą również zawierać lata logiki zgodności wbudowanej bezpośrednio w kod. Modernizacja może przypadkowo usunąć mechanizmy kontroli, których istnienia spodziewają się audytorzy.
Ocena ryzyka bezpieczeństwa gwarantuje, że uwierzytelnianie, autoryzacja, szyfrowanie i ślady audytu zostaną zachowane lub ulepszone podczas okresu przejściowego. Zgodność nie jest czymś, co „dodaje się później”. Musi być uwzględniana w każdym etapie modernizacji.
Pomiar ryzyka operacyjnego i przestojów
Ryzyko operacyjne to nie tylko przestoje. Obejmuje ono obniżoną wydajność, opóźnione raportowanie, ręczne obejścia problemów i zwiększone obciążenie działów wsparcia. Pomiar tych ryzyk wymaga współpracy między zespołami technicznymi i biznesowymi.
W Grupie SKM przekładamy ryzyko operacyjne na język biznesowy, aby umożliwić Ci podejmowanie świadomych decyzji. Ta przejrzystość jest niezbędna do podejmowania decyzji dotyczących strategii modernizacji starszego oprogramowania , które łączą szybkość ze stabilnością.
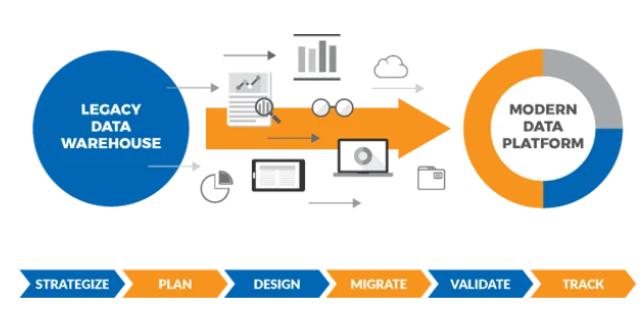
Odkrycie i analiza bazowa systemu
Odkrywanie to etap, w którym modernizacja albo odnosi sukces, albo po cichu zawodzi. Ta faza ustala faktyczną bazę odniesienia dotyczącą tego, jak Twoje systemy zachowują się obecnie – a nie jak powinny zachowywać się zgodnie z dokumentacją.
Analiza bazowa rejestruje wskaźniki wydajności, wzorce użytkowania, wskaźniki błędów i przepływy integracji. Tworzy punkt odniesienia, który pozwala mierzyć postępy i wykrywać regresję w przyszłości. Bez tej linii bazowej modernizacja staje się domysłem.
Projektuj, buduj i skaluj produkty cyfrowe w sposób kompleksowy tworzenie oprogramowania na zamówienie.
Dekompozycja architektury i mapowanie zależności
Dekompozycja nie polega na rozbijaniu systemów na części. Chodzi o zrozumienie, jak są one ze sobą połączone. Mapowanie zależności ujawnia powiązania na poziomie kodu, danych i procesów.
Ta faza identyfikuje, które komponenty mogą ewoluować niezależnie, a które wymagają skoordynowanych zmian. Bezpośrednio wspiera ona najlepsze praktyki modernizacji starszych systemów , zapobiegając przypadkowej fragmentacji architektury.
Planowanie i walidacja migracji danych
Planowanie migracji definiuje sposób, czas i miejsce przenoszenia danych oraz sposób weryfikacji ich poprawności. Mechanizmy walidacji muszą istnieć przed rozpoczęciem migracji, a nie po wystąpieniu problemów.
Ta faza obejmuje przebiegi równoległe, procesy uzgadniania i jasne kryteria wycofania. W Grupie SKM traktujemy migrację jako kontrolowany eksperyment z predefiniowanymi progami sukcesu.
Przyrostowe refaktoryzowanie i wymiana komponentów
Przyrostowe refaktoryzowanie zmniejsza ryzyko poprzez ograniczenie zakresu zmian. Zamiast wymieniać całe systemy, modernizujesz komponenty w izolacji, zachowując jednocześnie działanie systemu.
To podejście:
Stopniowe zmiany są początkowo wolniejsze, ale z czasem znacznie bezpieczniejsze. To podstawa zrównoważonej modernizacji.
Testowanie regresyjne i benchmarking wydajności
Modernizacja kończy się niepowodzeniem, gdy testy regresyjne są słabe. Systemy wydają się funkcjonalne, ale zachowują się inaczej pod rzeczywistym obciążeniem lub w warunkach brzegowych.
Testy regresyjne weryfikują równoważność funkcjonalną, a testy wydajnościowe gwarantują, że modernizacja nie powoduje opóźnień ani regresji skalowalności. Kontrole te zamykają pętlę między zamierzeniem a rezultatem, wzmacniając dyscyplinę w ograniczaniu ryzyka związanego z modernizacją starszych systemów .
Modernizacja odnosi sukces, gdy zasady są silniejsze niż narzędzia. Technologie się zmieniają. Dostawcy usług chmurowych ewoluują. Ramy czasowe wygasają. Tym, co Cię chroni, jest dyscyplina. W Grupie SKM najlepsze praktyki modernizacji starszych modeli opierają się na powściągliwości inżynieryjnej i świadomości biznesowej, a nie na adaptacji trendów.
Pierwszą zasadą jest ciągłość. Twój dotychczasowy system istnieje, ponieważ nadal zapewnia wartość. Modernizacja musi zachować tę wartość na każdym kroku. Drugą zasadą jest odwracalność. Każda ważna decyzja powinna być technicznie odwracalna, dopóki nie zostanie potwierdzona w praktyce. Trzecią zasadą jest przejrzystość. Zawsze powinieneś wiedzieć, co się zmieniło, dlaczego i jak to cofnąć.
Gdy te zasady kierują realizacją, modernizacja staje się przewidywalna. Bez nich nawet najlepsi architekci polegają na szczęściu.
Architektura jest podstawowym mechanizmem kontroli ryzyka w modernizacji. Słaba architektura potęguje niepewność. Silna architektura ją absorbuje.
Przemyślana strategia architektoniczna zapobiega kaskadowym awariom poprzez rozdzielenie problemów, ograniczenie promienia rażenia i umożliwienie równoległej ewolucji. W ten sposób unikanie awarii modernizacji starszych systemów staje się efektem architektonicznym, a nie nadzieją projektu.
Ryzyko można zmniejszyć poprzez:
Architektura to nie dokumentacja. To kontrakt operacyjny między dzisiejszymi systemami a jutrzejszymi ambicjami.
Wybór właściwego podejścia do modernizacji (rehosting, refaktoryzacja, rearchitektura)
Nie ma uniwersalnej ścieżki modernizacji. Rehosting zmniejsza ryzyko infrastrukturalne, ale chroni architekturę. Refaktoryzacja poprawia łatwość utrzymania, ale wymaga głębszego zrozumienia systemu. Rearchitektura umożliwia transformację, ale wiąże się z najwyższym ryzykiem krótkoterminowym.
Solidna strategia modernizacji starego oprogramowania łączy w sobie podejścia. Stosujesz każde z nich tam, gdzie zapewnia maksymalną wartość przy minimalnych zakłóceniach. Strategia nie polega na wyborze jednej metody, lecz na ich inteligentnym uporządkowaniu.
Dostosowanie celów biznesowych do celów modernizacji technicznej
Modernizacja kończy się fiaskiem, gdy liderzy biznesowi i zespoły techniczne optymalizują swoje działania pod kątem różnych rezultatów. Zespoły technologiczne dążą do elegancji. Liderzy biznesowi dążą do stabilności i rozwoju.
Dopasowanie oznacza przełożenie zmian technicznych na wpływ na biznes. Każda inicjatywa modernizacyjna powinna jasno odpowiedzieć na jedno pytanie: w jaki sposób zmniejsza to ryzyko, koszty lub czas wprowadzania produktu na rynek? Gdy istnieje dopasowanie, priorytetyzacja staje się obiektywna, a nie polityczna.
Zarządzanie długiem technicznym w trakcie postępującej modernizacji
Dług techniczny nie znika sam z siebie. Postępowa modernizacja pozwala go spłacić bez wstrzymywania działalności.
Zarządzanie długiem wymaga przejrzystości. Monitorujesz, gdzie występuje zadłużenie, jak wpływa ono na szybkość realizacji i kiedy staje się nieakceptowalne. To przekształca zadłużenie z emocjonalnego argumentu w skwantyfikowany czynnik ryzyka – kluczowy dla minimalizacji ryzyka związanego z modernizacją starszych systemów .
Definiowanie wskaźników sukcesu i kluczowych wskaźników efektywności modernizacji
Bez metryk sukces modernizacji staje się subiektywny. Kluczowe wskaźniki efektywności (KPI) muszą obejmować stan techniczny i wyniki biznesowe.
W Grupie SKM definiujemy sukces poprzez stabilność systemu, częstotliwość wdrożeń, redukcję incydentów i trendy w zakresie kosztów operacyjnych. Te wskaźniki gwarantują, że modernizacja przynosi mierzalny postęp, a nie tylko zmiany w architekturze.
Planowanie skalowalności i gotowości do pracy w chmurze
Skalowalność nie jest osiągana poprzez migrację do chmury. Osiąga się ją poprzez projektowanie z myślą o elastyczności, bezstanowości i odporności na awarie.
Gotowość do pracy w chmurze wymaga zmian w architekturze, wdrażaniu i operacjach. Wczesne zaplanowanie pozwala uniknąć kosztownych przeprojektowań w przyszłości i zapewnia długoterminową odporność.
Zoptymalizuj wydajność i bezpieczeństwo dzięki kompleksowemu usługi informatyczne.
Modernizacja bez zarządzania prowadzi do fragmentacji. Nadmiar zarządzania prowadzi do paraliżu. Skuteczne zarządzanie modernizacją dziedzictwa równoważy autonomię z kontrolą.
Zarządzanie definiuje uprawnienia decyzyjne, standardy architektoniczne i progi ryzyka. Zapewnia zespołom podążanie w tym samym kierunku, zachowując jednocześnie elastyczność realizacji. Co najważniejsze, zapewnia rozliczalność – czego często brakuje w starszych środowiskach.
W DevOps nie chodzi o szybkość. Chodzi o kontrolę poprzez automatyzację. Zautomatyzowane procesy ograniczają błędy ludzkie, egzekwują standardy i zapewniają powtarzalne rezultaty.
Aby zmniejszyć ryzyko związane z modernizacją starszych systemów , automatyzacja musi być wprowadzana równolegle z modernizacją, a nie po niej. Obejmuje to zautomatyzowane testowanie, wdrażanie, monitorowanie i mechanizmy wycofywania. Automatyzacja przekształca ryzyko z nieprzewidywalnego w możliwe do opanowania.
Procesy CI/CD dla przejść ze starszej wersji na nowszą
Procesy CI/CD wymuszają spójność w różnych środowiskach. Gwarantują, że każda zmiana przechodzi przez tę samą ścieżkę walidacji, co zmniejsza ryzyko dryftu konfiguracji i nieoczekiwanych awarii.
Strategie automatycznego testowania starszych baz kodu
W starszych systemach często brakuje testów. Wprowadzenie testów automatycznych stopniowo chroni zachowanie systemu, umożliwiając jednocześnie bezpieczną refaktoryzację. Testowanie nie polega na procentowym pokryciu, lecz na ochronie logiki biznesowej.
Przełączanie funkcji i kontrolowane wdrażanie
Przełączniki funkcji umożliwiają udostępnianie kodu bez jego aktywacji. Kontrolowane wdrożenia ograniczają ryzyko i umożliwiają szybkie wycofanie w przypadku wystąpienia problemów.
Obserwowalność, monitorowanie i reagowanie na incydenty
Nie da się zarządzać czymś, czego nie widać. Obserwowalność zapewnia wgląd w zachowanie systemu w czasie rzeczywistym, umożliwiając szybsze wykrywanie i rozwiązywanie problemów pojawiających się podczas modernizacji.
Mechanizmy wycofywania i projektowanie architektury odpornej na awarie
Wycofanie nie jest porażką. To mechanizm bezpieczeństwa. Wcześniejsze zaprojektowanie ścieżek wycofania zapobiega podejmowaniu decyzji pod presją w panice.
Strategie wdrażania bez przestojów
Wdrożenia bez przestojów chronią przychody i zaufanie klientów. Wymagają koordynacji między infrastrukturą, projektem aplikacji i operacjami – ale można je osiągnąć dzięki dyscyplinie.
Modernizacja starszych systemów nie polega na zastępowaniu ich nowymi. Chodzi o zastąpienie niepewności kontrolą. Kiedy strategia, architektura, zarządzanie i automatyzacja współdziałają ze sobą, ryzyko staje się widoczne i możliwe do opanowania.
W Grupie SKM pomagamy w modernizacji bez psucia tego, co już działa. Dzięki dyscyplinie w zarządzaniu ryzykiem modernizacji starszego oprogramowania , modernizacja staje się przewagą konkurencyjną, a nie zagrożeniem dla firmy.
Jakie są największe zagrożenia związane z modernizacją starszych systemów?
Do największych zagrożeń zalicza się uszkodzenie danych, nieplanowane przestoje, ukryte zależności, luki w zabezpieczeniach i brak zgodności między celami biznesowymi i technicznymi.
W jaki sposób organizacje mogą skutecznie ograniczyć ryzyko związane z modernizacją starszych systemów?
Realizują to poprzez ustrukturyzowaną ocenę ryzyka modernizacji starszych systemów , stopniowe dostarczanie, silne zarządzanie i kontrole oparte na automatyzacji.
Jaką rolę odgrywa architektura w zapobieganiu niepowodzeniom modernizacji?
Architektura definiuje granice, ogranicza wpływ awarii i umożliwia bezpieczną ewolucję, co odgrywa kluczową rolę w unikaniu niepowodzeń modernizacji starszych systemów .
Kiedy modernizację starszych systemów należy przeprowadzać stopniowo?
Modernizację stopniową zaleca się w przypadku systemów o krytycznym znaczeniu dla działalności, złożonych i słabo udokumentowanych — co ma miejsce w większości środowisk korporacyjnych.
Jak zarządzanie wpływa na sukces modernizacji istniejących systemów?
Zarządzanie zapewnia spójność, rozliczalność i dostosowanie ryzyka do potrzeb wszystkich zespołów, co ma bezpośredni wpływ na wyniki modernizacji.
Które branże są najbardziej narażone na ryzyko związane z modernizacją starszych systemów?
Branże, w których obowiązują wysokie wymogi regulacyjne i które wymagają zachowania ciągłości działania — takie jak finanse, opieka zdrowotna, logistyka i produkcja — są najbardziej narażone na ryzyko i odnoszą największe korzyści ze stosowania zdyscyplinowanych strategii modernizacji.
Zmień przestarzałe oprogramowanie w nowoczesne i wydajne narzędzie. Zobacz nasze podejście.
Zobacz więcej
Komentarze