

At SKM Group, we spend a lot of time talking with decision-makers who feel pressure to modernize simply because their systems are old. Age, however, is not a technical argument. Modernization is not a moral obligation, and legacy does not automatically mean inefficient, risky, or obsolete. If you are responsible for business continuity, revenue protection, and long-term technical strategy, your real task is not to modernize fast—but to modernize wisely.
Modernization discussions often start with emotion: fear of being left behind, fear of unsupported technology, fear of future failure. At SKM Group, we reverse that logic. We begin with engineering facts, architectural maturity, and measurable risk.
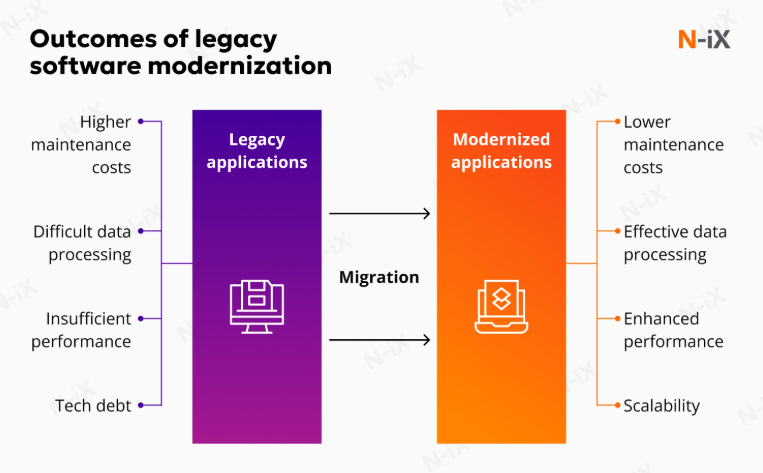
Understanding when not to modernize legacy systems requires defining what “not modernizing” actually means and what it does not.
Choosing not to modernize does not mean freezing a system in time or ignoring its weaknesses. In practice, it means deliberately deciding to keep the core architecture intact while maintaining operational stability, security, and performance at a level aligned with business needs.
You are not rejecting progress. You are rejecting unnecessary change. This approach often includes controlled maintenance, targeted refactoring, infrastructure isolation, and defensive security hardening. The system continues to evolve, just not through disruptive architectural replacement.
From a business standpoint, this choice is often invisible to users—and that is exactly the point. Stability becomes the feature.
At SKM Group, we look at legacy platforms through a strictly technical lens before recommending any transformation. A system may be old, yet technically sound. If its architecture is deterministic, well-understood, and behaves predictably under load, modernization becomes a risk rather than an improvement.
Key criteria often include runtime stability, data consistency, fault tolerance, and the absence of architectural bottlenecks that limit business growth. If the system meets these conditions, the technical argument for modernization weakens significantly.
Achieve measurable results while we manage execution through IT outsourcing.
One of the most persistent myths is that legacy systems are automatically insecure. In reality, many legacy platforms operate in closed, tightly controlled environments with limited attack surfaces. Security incidents often arise during modernization, not before it.
Another misconception is that modern systems are cheaper to maintain. Initial development costs may be lower, but long-term complexity, cloud sprawl, and vendor dependency frequently reverse the expected savings. Avoiding modernization is not technical stagnation; it is strategic restraint.
You often face pressure from internal innovation teams or external consultants pushing for modernization as a symbol of progress. But technical leadership requires resisting symbolic decisions that put operational continuity at risk.
Legacy systems often sit at the heart of billing engines, transaction processors, or settlement platforms. These systems are not innovation playgrounds. They are machines built for reliability, not experimentation. Replacing them introduces uncertainty into areas where failure is not tolerated.
At SKM Group, we remind our clients that innovation belongs at the edges of the architecture, not always at its core.
In regulated industries, modernization is rarely just a technical project. It is a legal and compliance challenge. Legacy systems often carry certifications, audits, and validations accumulated over decades. Rebuilding them means restarting that entire process.
From a technical governance perspective, keeping a compliant legacy system is often safer than re-certifying a new one with unproven operational history. In such environments, stability is not conservative—it is responsible.
Every legacy system modernization decision must start with architecture, not tooling trends. Architecture tells the truth about risk.
Mature architectures tend to be boring, and boring systems are reliable. If your legacy platform has survived peak loads, market crashes, and regulatory changes without systemic failure, it has already proven its value in production conditions that modern systems have never faced.
Replacing a mature architecture with a new one resets that reliability clock to zero. From a risk standpoint, this is a downgrade, not an upgrade.
Not all technical debt is equal. Some legacy systems are complex because they encode decades of business logic that no documentation can fully explain. Rewriting such systems often removes “invisible logic” that developers do not even know exists.
A proper assessment distinguishes between accidental complexity and essential complexity. Eliminating the wrong one can break revenue-critical behavior.
Legacy platforms sometimes depend on proprietary components that are expensive but extremely stable. Modern alternatives may promise openness but introduce layers of abstraction that increase failure points.
The question is not whether dependency exists, but whether it is predictable and controllable. In many cases, legacy dependencies are already fully amortized and operationally mastered.
A common fear is the shrinking pool of legacy engineers. In practice, this risk is often overstated. Many legacy platforms require fewer changes precisely because they are stable. A small, specialized team can maintain them effectively with proper documentation and support contracts.
Moreover, modern stacks also suffer from rapid skill obsolescence. The talent risk simply moves, it does not disappear.
Legacy does not mean isolated. Many older systems integrate reliably through message queues, file-based interfaces, or stable APIs. If integration works and does not block business evolution, modernization brings little architectural benefit.
In such cases, the legacy system functions as a processing core while modern layers evolve around it. This hybrid model is often the safest long-term strategy.
Modernization discussions often focus on technology, but the real constraint is economic reality. Understanding legacy modernization cost vs value requires looking beyond development budgets.
Modernization costs are not limited to development. They include testing, parallel operations, data reconciliation, compliance validation, and rollback planning. These costs accumulate long before the new system delivers value.
At the same time, operational continuity becomes fragile. Even small delays or defects can cascade into customer-facing failures.
Rewriting a system recreates known functionality at high cost, while unknowingly losing edge-case behavior. Maintaining a legacy system preserves proven outcomes with predictable effort.
The most expensive systems are not the ones that look old, but the ones that never quite work as expected after modernization.
In our experience at SKM Group, the following cost factors are frequently underestimated:
Return on investment must be measured against realistic outcomes, not optimistic projections. If modernization does not unlock new revenue streams, reduce risk, or significantly lower operating costs, the ROI case collapses.
A stable legacy system with predictable expenses often delivers better long-term value than a modern platform with uncertain behavior.
Risk is a cost, even if it does not appear on a balance sheet. Data loss, downtime, and reputational damage must be priced into modernization decisions. When you do that honestly, the financial argument for keeping legacy systems becomes much stronger.
Adapt quickly to changing demands with flexible IT services.
Every hour spent stabilizing a new system is an hour not spent improving customer experience, expanding markets, or optimizing processes. Migration consumes organizational energy at a massive scale.
If your legacy system already supports the business without blocking growth, modernization may be the most expensive distraction you can choose.
Across global enterprises, legacy systems still in use are often those that quietly do their job without drama. They are rarely visible in marketing decks, yet they carry enormous operational weight. At SKM Group, we see this pattern repeatedly: systems that were engineered for a narrow, well-defined purpose often outperform newer platforms precisely because they were never designed to be flexible.
Legacy platforms excel when workloads are stable, predictable, and deeply optimized. Over years—or decades—these systems have been tuned at every layer: database schemas shaped around real queries, batch processes aligned with business cycles, and error-handling logic refined through real incidents rather than theoretical models. What you end up with is not technical elegance, but operational mastery.
Another reason these systems continue to perform is organizational alignment. Business users have adapted their processes to the system’s behavior, not the other way around. That alignment reduces friction, training costs, and operational surprises. From a technical governance perspective, this symbiosis is extremely hard to replicate in a newly modernized environment.
The reasons to keep legacy systems are rarely emotional. They are grounded in predictability, control, and proven outcomes. Predictable system behavior under load is not a luxury—it is a requirement in environments where revenue, safety, or compliance are on the line. Legacy systems often behave the same way today as they did ten years ago, and that consistency is a strategic asset.
Mature monitoring and maintenance processes also play a critical role. Over time, teams learn exactly where a system fails, how it degrades, and how to recover it. Alert thresholds are meaningful, runbooks are accurate, and incident response is muscle memory. Modern systems, by contrast, often fail in new and unexpected ways.
Equally important is the deep alignment with existing business logic. Legacy codebases frequently encode complex rules that no longer exist in documentation or human memory. Removing or rewriting that logic introduces silent risk. If the system delivers correct outcomes and there are no functional gaps despite outdated technology, technical leadership demands restraint rather than reinvention.
The risks of modernizing legacy software are often discussed in abstract terms, but their impact is very real. Data migration alone represents a major threat to integrity. Legacy databases frequently contain implicit assumptions, edge cases, and historical anomalies that do not translate cleanly into modern schemas. Even small inconsistencies can lead to financial discrepancies or reporting failures months after go-live.
System downtime is another underestimated risk. Even with parallel environments and phased rollouts, real-world cutovers are rarely clean. Temporary service disruptions can ripple across dependent systems, partners, and customers. For revenue-generating platforms, this exposure is unacceptable.
One of the most dangerous risks is the loss of embedded business logic during refactoring. Developers modernizing a system often simplify code they do not fully understand, removing behaviors that appear redundant but are actually critical. Security risks can also increase when partial modernization creates architectural seams—new components expose interfaces that were never designed to be public.
Finally, modern platforms often introduce new forms of vendor lock-in. Cloud-native services promise speed, but they bind your architecture to pricing models, roadmaps, and constraints outside your control. From a long-term risk perspective, this trade-off must be evaluated with extreme care.
Build modular, scalable platforms through custom software development.
The debate around legacy system modernization vs replacement is fundamentally about risk distribution over time. Full replacement concentrates risk into a single, high-impact event. Incremental modernization spreads risk, but extends it over a longer period. Neither option is inherently safer; the safer choice depends on system criticality and tolerance for failure.
Technical feasibility matters more than ambition. Some architectures can be refactored safely because their boundaries are clean and their logic is well understood. Others are so entangled with business processes and external integrations that rebuilding them is closer to reverse engineering than development.
Existing integrations and APIs amplify this risk. Every downstream dependency becomes a potential failure point during replacement. Long-term maintainability must be assessed honestly: a modern system that requires constant change may be less maintainable than a legacy system that rarely needs modification.
At SKM Group, we often advise choosing the path that minimizes irreversible decisions. Once a legacy system is replaced, its knowledge is gone forever.
There are clear strategic scenarios where when not to modernize legacy systems becomes the only rational choice. Systems with low change frequency and stable requirements rarely benefit from architectural upheaval. If business rules have not changed in years, forcing change at the technical layer introduces unnecessary volatility.
Legacy platforms that support core revenue streams deserve special caution. These systems are not experiments. They are financial engines. Applications with high re-certification or re-validation costs, especially in regulated industries, face modernization barriers that can outweigh any technical benefit.
Systems with limited user interfaces and no UX pressure are another strong candidate for preservation. If users never interact directly with the platform, modern front-end paradigms offer no value. In environments with strict regulatory oversight, maintaining a known, compliant system is often safer than reintroducing regulatory uncertainty.
Finally, many legacy systems act as back-end processing engines. They transform data, reconcile transactions, or calculate outcomes. As long as they do this correctly and on time, their internal technology stack is irrelevant to business success.
At SKM Group, we believe modernization is a tool, not a goal. The right legacy system modernization decision is the one that protects your business while enabling future growth. Sometimes that decision leads to transformation. Just as often, it leads to disciplined preservation.
Keeping a legacy system is not failure. It is a signal that engineering discipline, risk awareness, and business understanding are guiding your strategy. The question you should ask is not “Is this system old?” but “Does this system still serve us better than any alternative?”
When not to modernize legacy systems from a technical standpoint?
When the system is stable, compliant, predictable under load, and not blocking business evolution, modernization increases risk without delivering proportional value.
How do you evaluate legacy modernization cost vs value?
By including operational risk, downtime exposure, hidden migration costs, and opportunity cost—not just development budgets.
What are the biggest risks of modernizing legacy software?
Data integrity loss, service disruption, removal of undocumented business logic, new security gaps, and long-term vendor lock-in.
Is legacy system modernization always better than replacement?
No. Both options carry risk. The safer choice depends on system criticality, architectural clarity, and tolerance for failure.
Why are legacy systems still in use in modern enterprises?
Because they are optimized, reliable, compliant, and aligned with real business processes in ways modern systems often are not.
How can architects decide whether to keep or modernize a legacy system?
By focusing on architecture maturity, business impact, risk concentration, and long-term control—not technology trends.
Zmień przestarzałe oprogramowanie w nowoczesne i wydajne narzędzie. Zobacz nasze podejście.
Zobacz więcej
Komentarze